Take Your IT Skill to the Next Level with i3
AVAILABLE
PROMO
Enterprise
Customers
Students
Classes
Delivered
WHY TRAINING
WITH i3?
i3 training is the company’s flagship service, and it is widely considered as the best training service in the IT business. i3 is committed to providing individuals and businesses with high-quality training that is essential to their growth and success. Customers have constantly applauded the organization for its professionalism, experience, and commitment to offering excellent training programs, showing the company’s focus on providing outstanding training services.
When it comes to training with i3, individuals and businesses can expect nothing but the best. Supported by highly experienced trainers, individuals who take i3 training, whether they are beginners or experienced professionals, will gain the information, skills, and competence required to stay ahead in the IT industry.
Certified Trainers
Costumized Training
Certified Training Center
Best Training Partner for 4 Consecutive Years from Red Hat
COMPANIES THAT HAVE TRAINED WITH i3



















































DISCOVER OUR ULTIMATE TRAINING PROGRAM
Mastering Ansible Automation: A Comprehensive i3 Infrastructure Training
By joining training class at i3, trainees should be able to better understand the fundamentals of system administration and handle operating systems more effectively to get ansible automation certification. Through this course, trainees will be prepared to handle the Linux operating system in their corporate environment and give value added to their company.
Red Hat System Administration I (RH124)
Red Hat System Administration I (RH124) is intended for IT professionals with no prior knowledge with Linux system administration. The course equips students with Linux administration skills by focusing on essential administration tasks. By presenting important command-line ideas and enterprise-level tools, this course also serves as a foundation for students who want to work as full-time Linux system administrators.
Red Hat System Administration II (RH134)
Red Hat System Administration II (RH134) is the second phase of the RHCSA training track for IT professionals who have completed Red Hat System Administration I (RH124). The course delves deeper into core Linux system administration skills such as storage configuration and management, installation and deployment of Red Hat® Enterprise Linux®, management of security features such as SELinux, control of recurring system tasks, boot process management and troubleshooting, basic system tuning, and command-line automation and productivity.
Red Hat Certified System Administration Rapid Track course (RH199)
The RHCSA Rapid Track course (RH199) uses Red Hat® Enterprise Linux® 9 and is intended for those who have prior experience with Linux administration. This course includes the important information of Red Hat System Administration I (RH124) and Red Hat System Administration II (RH134), reviewing the tasks at a faster pace.
Red Hat Enterprise Linux Automation with Ansible (RH294)
Red Hat Enterprise Linux Automation with Ansible (RH294) is intended for Linux administrators and developers that need to automate repeatable and error-prone tasks for system provisioning, configuration, application deployment, and orchestration.
Becoming a Certified PostgreSQL Expert with i3 Training
Trainees will be expected to gain a greater understanding of the potential of PostgreSQL and SQL database technology, as well as the ability to design better and more effective solutions that meet their business goals, thanks to this course. The PostgreSQL training program is designed to give participants an in-depth knowledge of SQL databases, especially PostgreSQL. During the course, trainees will learn the fundamental ideas and features of PostgreSQL, such as data modelling, database administration and management, and performance and tuning.
PostgreSQL I i3’s Exclusive Curriculum
This course is an exclusive curriculum from i3 that will give all you need to know to be a PostgreSQL DBA. You will learn about the fundamental PostgreSQL Administration Task.
Red Hat OpenShift Administration II: Operating a Production Kubernetes Cluster (DO280)
Red Hat OpenShift Administration II: Operating a Production Kubernetes Cluster (DO280) prepares OpenShift Cluster Administrators to perform daily administration tasks on clusters that host applications provided by internal teams and external vendors, enable self-service for cluster users with different roles, and deploy applications that require special permissions such as CI/CD tooling, performance monitoring, and security scanners.
Red Hat OpenShift Developer II: Building Kubernetes Applications (DO288)
Red Hat OpenShift Developer II: Building Kubernetes Applications (DO288) teaches you how to design, build, and deploy containerized software applications on an OpenShift cluster. Whether you are migrating existing applications or developing container-native applications, you will learn how to boost developer productivity using Red Hat® OpenShift Container Platform, a containerized application platform that allows enterprises to manage container deployments and scale their applications using Kubernetes.
DevOps Toolchains I i3’s Exclusive Curriculum
DevOps ToolChain with Docker, Ansible, Git, Jenkins, Nexus Repository, and K8s training covers the entire CI/CD, Development, and Deployment process, as well as the models utilized at each stage of the lifecycle.
DevSecOps Toolchains I i3’s Exclusive Curriculum
DevSecOps ToolChain with SAST, DAST, Ansible, Jenkins, and OpenShift training covers the entire CI/CD, Development, and Deployment process, as well as the models utilized at each stage of the life cycle.
OpenStack RHCSA Certification Bootcamp with i3
Trainees will study the fundamental ideas and best practices for developing, implementing, and managing cloud environments with OpenStack. Trainees will gain a better understanding of the advantages and benefits of utilizing private cloud in their business operations, such as flexibility, security, and scalability.
Trainees will be expected to be able to further leverage the possibilities of Private Cloud technology and offer added value to their companies because of this training.
Red Hat OpenStack Administration I: Core Operations for Cloud Operators (CL110)
Red Hat OpenStack Administration I: Core Operations for Domain Operators (CL110) teaches you how to run and manage a production Red Hat OpenStack Platform (RHOSP) single site overcloud. You will learn how to construct secure project environments in which to provision resources and manage security capabilities required by cloud users to deploy scalable cloud apps. You will learn about OpenShift integration with load balancers, identity management, monitoring, proxies, and storage. In this course, you will also improve your troubleshooting and Day 2 operations skills.
Red Hat OpenStack Administration II: Infrastructure Configuration for Cloud Administration (CL210)
Red Hat OpenStack Administration II: Day 2 Operations for Cloud Operators (CL210) is intended for cloud operators, service administrators, and automation engineers that administer and manage a full-featured hybrid and private cloud-computing environment utilizing Red Hat OpenStack Platform. You will learn how to manage, monitor, troubleshoot, and scale a Red Hat OpenStack Platform infrastructure. This course focuses on configuring metrics, policies, and architecture to enable enterprise cloud applications and daily operations using the OpenStack Client command-line user interface.
Defend and Attack: i3’s Cybersecurity Ethical Hacker Certification Training
i3’s cybersecurity training program aims to give a thorough awareness of cybersecurity ethical hacker certification and capabilities in defending systems and data from cyberthreats. Trainees who obtain this certification will have the skills, knowledge, and ability to safeguard organizations that required that required in today’s business.
Certified Ethical Hacker (CEH)
A Certified Ethical Hacker is an expert who works in a red team environment to attack computer systems and get access to networks, applications, databases, and other critical data on secured systems. A C|EH® understands strategies for attack, the use of innovative attack vectors, and mimics the skills and creativity of hostile hackers. Unlike malicious hackers and actors, Certified Ethical Hackers operate with the permission of the system owners and take all efforts to ensure the results remain private. Bug bounty researchers are professional ethical hackers who employ their attack talents to discover flaws in systems.
Computer Hacking Forensic Investigator (CHFI)
The EC-Council’s Hacking Forensic Investigator (CHFI) curriculum is the only comprehensive ANSI recognized, lab-focused program on the market that provides businesses with vendor-neutral digital forensics training. C|HFI gives attendees a solid understanding of digital forensics by delivering a rigorous and methodical approach to digital forensics and evidence analysis that includes focuses on the Dark Web, IoT, and Cloud Forensics. This program’s tools and procedures will prepare learners to conduct digital investigations utilizing cutting-edge digital forensics technologies.
Certified Chief Information Security Officer (CISO)
The Certified CISO (CCISO) program is the first of its kind, focusing on developing top-level information security executives through training and certification. The CCISO focuses not only on technical knowledge, but also on the application of information security management principles from an executive management perspective. The training was designed for current and aspiring CISOs by sitting CISOs.
Certified Chief Defender (CND)
ND is a network security course aimed to assist businesses in developing and deploying the most comprehensive network defence system.
Certified Penetration Testing Professional (CPENT)
C|PENT is a multidisciplinary course that provides extensive hands-on training in a wide range of critical skills, including advanced Windows attacks, Internet of Things (IoT) and Operational Technology (OT) systems, filtered network bypass techniques, exploit writing, single and double pivoting, advanced privilege escalation, and binary exploitation. In summary, there is no other program like it in the world!
Certified Incident Handler (ECIH)
The current version of the EC-Council’s Certified Incident Handler (E|CIH) program was conceived and developed in partnership with cybersecurity and incident handling and response practitioners from around the globe. It is a complete specialist-level program that imparts information and skills that organizations require to effectively handle post-breach implications by mitigating the impact of the incident from both a financial and a reputational perspective.
Certified Secure Computer User (CSCU)
The CSCU training program is designed to provide students with the knowledge and skills needed to protect their digital assets. The software is designed to teach students interactively about the whole range of information security concerns they face, from identity theft and credit card fraud to physical safety. The skills learned during this program will not only assist students in identifying these threats, but also in effectively mitigating them.
i3’s Comprehensive Middleware Training for Performance Enhancement
Trainees will get the skill needed to handle complicated technical problems and improve the performance of their business middleware by learning JBoss Application Administration. As a result of this program, trainees are expected to enhance their skills in creation and JBoss app administration to offer value to their business.
Jboss Application Administration (AD248)
Red Hat JBoss Application Administration I teach you the best methods for installing and configuring Red Hat® JBoss® Enterprise Application Platform (JBoss EAP) 7. Learn the key, real-world tasks that a system administrator needs to know to deploy and manage applications on JBoss EAP through hands-on experiments.
Red Hat Jboss Application Administration II (AD348)
Red Hat JBoss Application Administration II (AD348) prepares students to provision and manage Red Hat® JBoss® Enterprise Application Platform (JBoss EAP) in large-scale production environments. Intended for experienced administrators, this course provides a deeper understanding of how to work with JBoss EAP by focusing on installation, clustering, deployments, scripting, management, messaging, and security in order to build on the skills established in Red Hat JBoss Application Administration I (AD248).
Tailored to Your Needs: i3’s Custom Curriculum Program
Expert consultants from i3 developed and curated the whole curriculum that match your business needs.
1. PostgreSQL
2. DevOps Toolchains
3. DevSecOps Toolchains
4. Automation Test Catalon
5. Elastic Stack Administration
TRAINING CALENDAR
RANGE OF BENEFITS FOR YOU
As a well-known IT training course, i3 will provide a comprehensive service based on your company’s need.
Here are some benefits if you take training at i3.
CERTIFICATES


COURSE MATERIALS
The material is complete from A to Z, with the essential points provided starting with the basics.
HANDS-ON LABS
Participants can immediately practice in the lab – can immediately try or practice according to the material being taught.


FREE CONSULTATION
Trainees can ask questions and get free consultation about the subject for two weeks after the training. So, after the class is ended, students still get the after class as well as invited to WhatsApp group.
OUR CUSTOMER TESTIMONY

Ramadhan Zandhy Pratama
Thank you to i3 and the instructor for giving extremely useful knowledge and material.

Muchamad Fajar Kurniawan
Great! The training is very extensive and systematic.

Yhozigma Harra Ramandha
Simple. Flexible. According to the needs.

Muhammad Hafizo Wazzakka
Excellent trainer.

Nauval Aryawiratama
The training offered is very valuable and easy to be implemented in the workplace. The material is detailed and informative, making it easier to understand overall.

Aji Neka Permana
i3 is a reliable training company.

Willy
The training was excellent; the instructor’s information was clear and well-presented.

Eric Tirtana
The trainer delivers the subject very clearly, making this training session easy to follow. Aside from that, the daily notes provided are beneficial for practicing the material taught on our own.
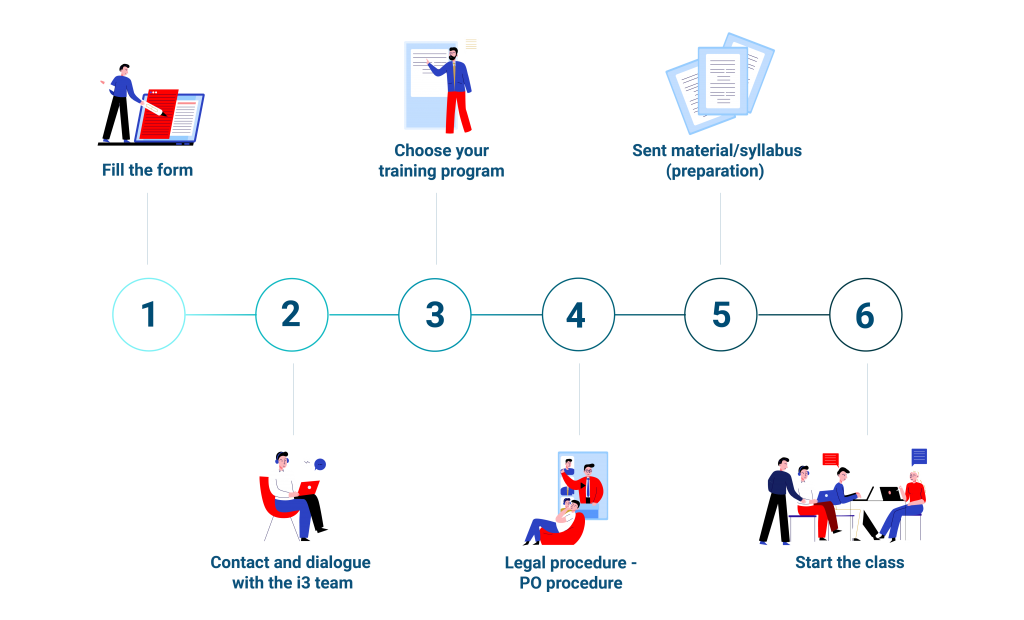
ENROLLMENT PROCESS

Yakin Keamanan Aplikasi Anda Sudah Andal? Cek di Sini
Aplikasi mobile kini telah menjadi urat nadi bagi keberlangsungan bisnis suatu perusahaan. Hanya saja, faktor keamanan aplikasi justru masih belum bisa berjalan seiring dengan pertumbuhan

Catat, Ini 8 Tren Keamanan Siber yang Siap Mendominasi 2023!
Keamanan siber saat ini sudah perhatian utama para pemimpin organisasi dan perusahaan di seluruh dunia. Hal ini tidak terlepas dari makin meningkatnya kejadian insiden keamanan

Apa Itu Patch Management dan Mengapa Harus Dilakukan Secara Berkala?
Lonjakan serangan siber di seluruh dunia, peningkatan kebutuhan untuk memproteksi software dan aplikasi berbasis web, hingga semakin meningkatnya kesadaran akan keamanan siber menjadi faktor pendorong
